For Bulk Orders email us at sales@enfotechindia.com OR call us at 9999109006
Safeguards of Network & systems in era cyber frauds
By addressing these key areas and adopting a proactive and holistic approach to cybersecurity, organizations can enhance the security posture of their systems and better protect against cyber attacks.
VJ
3/15/20242 min read
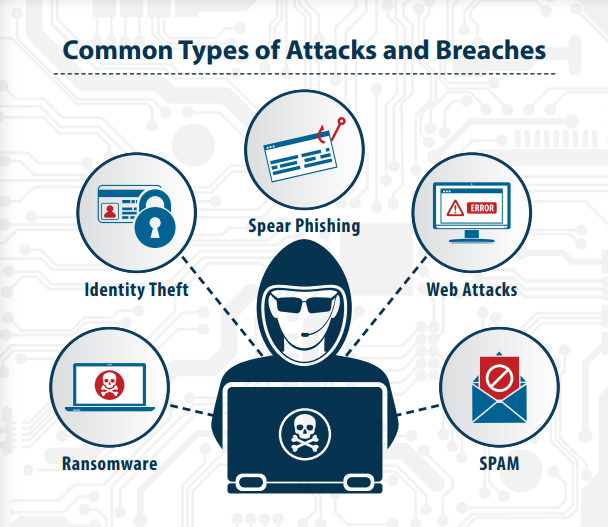
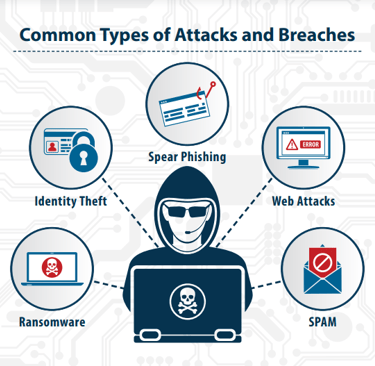
Ensuring that systems are sufficiently secure to be safeguarded from cyber attacks requires a comprehensive and multi-layered approach. Here are some key aspects to consider:
1. Risk Assessment and Management: Begin by conducting a thorough risk assessment to identify potential vulnerabilities and threats to your systems. Understand the value of your assets, the likelihood of various threats, and the potential impact of security breaches. Use this information to prioritize security measures and allocate resources effectively.
2. Strong Access Controls: Implement robust access controls to limit user privileges and restrict access to sensitive data and system resources. This includes using strong authentication methods such as multi-factor authentication (MFA), enforcing the principle of least privilege, and regularly reviewing and updating user permissions.
3. Regular Software Updates and Patch Management: Keep all software, including operating systems, applications, and firmware, up to date with the latest security patches and updates. Vulnerabilities in software can be exploited by cyber attackers, so timely patch management is essential to mitigate these risks.
4. Network Security: Secure your network infrastructure with firewalls, intrusion detection and prevention systems (IDS/IPS), and virtual private networks (VPNs). Segment your network to limit the spread of cyber attacks and protect critical assets. Implement strong encryption protocols to safeguard data in transit.
5. Data Encryption: Encrypt sensitive data both at rest and in transit to protect it from unauthorized access. Use strong encryption algorithms and key management practices to ensure the confidentiality and integrity of your data, especially when stored in cloud environments or transmitted over public networks.
6. Security Awareness Training: Educate employees about cybersecurity best practices and the importance of adhering to security policies and procedures. Regular training sessions can help raise awareness about common threats such as phishing, social engineering, and malware, empowering users to recognize and report suspicious activities.
7. Incident Response Planning: Develop a comprehensive incident response plan outlining the steps to be taken in the event of a security breach or cyber attack. Define roles and responsibilities, establish communication channels, and conduct regular drills to test the effectiveness of your response procedures.
8. Continuous Monitoring and Threat Intelligence: Implement robust monitoring tools and security information and event management (SIEM) systems to detect and respond to security incidents in real-time. Stay informed about the latest cyber threats and vulnerabilities by leveraging threat intelligence feeds and collaborating with industry peers and security experts.
9. Secure Development Practices: Adopt secure coding practices and conduct regular security reviews and code audits to identify and remediate potential vulnerabilities in software applications and development processes.
10. Compliance and Regulatory Requirements: Ensure compliance with relevant industry regulations and data protection laws such as GDPR, HIPAA, and PCI DSS. Implement controls and security measures that align with regulatory requirements to mitigate legal and financial risks associated with non-compliance.
By addressing these key areas and adopting a proactive and holistic approach to cybersecurity, organizations can enhance the security posture of their systems and better protect against cyber attacks. Remember that cybersecurity is an ongoing process that requires continuous monitoring, adaptation, and improvement to stay ahead of evolving threats. Contact Enfotech for safeguarding your hardware & network.

